Is Sharing Security Data The Best Way To Deter Cyber Criminals?
ten effective steps for preventing cyberattacks on your concern

Companies are vulnerable to cyberattacks because the world of applied science is constantly evolving, and cybercriminals know they tin can make a lot of money if they achieve their nefarious objectives.
Large corporations and pocket-size or medium-sized enterprises (SMEs) have to be proactive to prevent an attack because hackers are always looking to exploit any weaknesses in their cybersecurity procedures.
A successful cyberattack can lead to substantial data loss and theft of proprietary, employee, and customer data. Hackers have an arsenal of digital weapons, such as malware, Trojans, botnets, and distributed-deprival-of-service (DDoS) attacks, to disrupt concern operations, and information technology can be difficult to get infected systems running smoothly again. The all-time antivirus software may help thwart some of these threats, but you even so demand to take extra precautions to go along your company protected.
With this in mind, we nowadays 10 effective steps for preventing cyberattacks on your business.
1. Install top security antivirus software and endpoint protection

It costs more to lose data than to forestall its loss past investing in advanced cybersecurity software. Antivirus software and endpoint protection services offer value for money by establishing a firewall to protect your network from viruses and animal forcefulness attempts to access your systems. They scan your devices and portable disks for malware, preventing malicious actors from breaching your business' online shield.
The primal to using antivirus software is to go on it updated and with its protection settings set high. Read newsletters from the antivirus software service provider to learn about recent online threats, or visit its blog for more insights and analysis on cybercrime trends.
Endpoint protection involves securing all user devices connected to the company's network, such as laptops, tablets, printers, servers, smartwatches, and mobile phones. Endpoint Protection Platforms (EPPs) can remotely update and manage private devices, detect online threats and login attempts, and encrypt data to preclude unauthorized access.
2. Outsource protection needs to a cybersecurity business firm

Cybersecurity can be challenging for smaller businesses, some with limited budgets for their Information technology departments, others that can't afford a large squad of in-house online security experts, and those that struggle to recruit talented cybersecurity specialists.
Outsourcing cybersecurity to specialized firms brings skilled and dedicated Information technology professionals to monitor your network, cheque online threat exposure, and deal with the various cyberattacks prevalent nowadays. Moreover, outsourcing enables you to focus on your core business, knowing that the experts are up to date on current cyber risks and will deliver layered protection for your visitor.
Furthermore, external cybersecurity firms will assess your cyber policies, secure your networks, update your devices, and create filters to forestall spam. They volition too ready up firewalls for real-time protection and provide round-the-clock services.
3. Prepare online safety guidelines

Every business needs a cybersecurity policy outlining its guidelines for accessing the internet securely, protecting the visitor from liability, shielding employees from danger and exploitation, and ensuring customers accept a safe and reliable experience. The company must set up secure systems for conducting transactions to protect its customers from identity theft and financial loss.
Threats come from non only cybercriminals merely also former and electric current employees, rival companies, business partners, and poor internal cybersecurity measures. A company should plant rules on how employees employ company devices, transfer data safely, or share information on websites and social media platforms. In improver, colleagues should refrain from sharing their passwords to ensure greater control over information.
Finally, there should be guidelines for updating systems and software on time, every bit these patches guard against the latest online threats and vulnerabilities discovered by experts.
4. Protect employee information and shop information securely

Hackers use a method called social applied science, whereby they employ publicly bachelor data to manipulate people into sharing confidential information. Thus, companies should limit the amount of information they share online about their business and employees.
Unsecured data is an open up invitation to cybercriminals to come and take advantage. Businesses must store their data securely and have multiple information backups to safeguard sensitive data from cyber theft, loss, destruction, and natural disasters. Cull the right data storage service for your needs because the features that work well for ane company might not be platonic for your concern.
You lot should too consider using a secure data storage service that encrypts and stores your information online in real-time considering y'all never know when a cyberattack might happen.
5. Encrypt data when sharing or uploading online

To prevent cybercriminals from intercepting your data during transfers or online uploads, you must encrypt it outset or employ a cloud storage service that offers stop-to-finish data encryption. If you are using software to encrypt the data earlier storing it online, make sure to proceed the decryption key safe, or y'all volition lose your data.
Encrypt your network through the control panel settings or pay for a virtual private network (VPN) service to ensure your online interactions and data transfers are secure and bearding. Companies have a tendency to collect and store personally identifiable data, which can exist obtained by cybercriminals and used to steal identities and thus further compromise business organization data.
vi. Teach employees well-nigh online rubber

The switch to remote working due to the COVID-19 pandemic has exposed many non-tech-savvy employees to online threats, opening companies to cyberattacks. Hybrid working, a combination of in-function and work-from-home policies, also creates risks with employees, for example, connecting to unsecured public Wi-Fi networks to do their jobs.
Employees need to be upskilled on transferring data deeply, preventing unauthorized access to visitor networks, accessing dangerous websites, or falling for online scams. Phishing scams, whereby criminals pretend to be legitimate organizations to obtain personal information from employees, take become prevalent.
Bosses must create a workplace culture that understands the importance of cybersecurity, with regular preparation by professionals. There should exist a cyber incident response plan empowering employees to handle a data breach and report potential threats. Moreover, employees should exist encouraged to think before sending personal or sensitive information, especially if the asking to do and so sounds suspicious.
7. Create complex passwords or apply passphrases
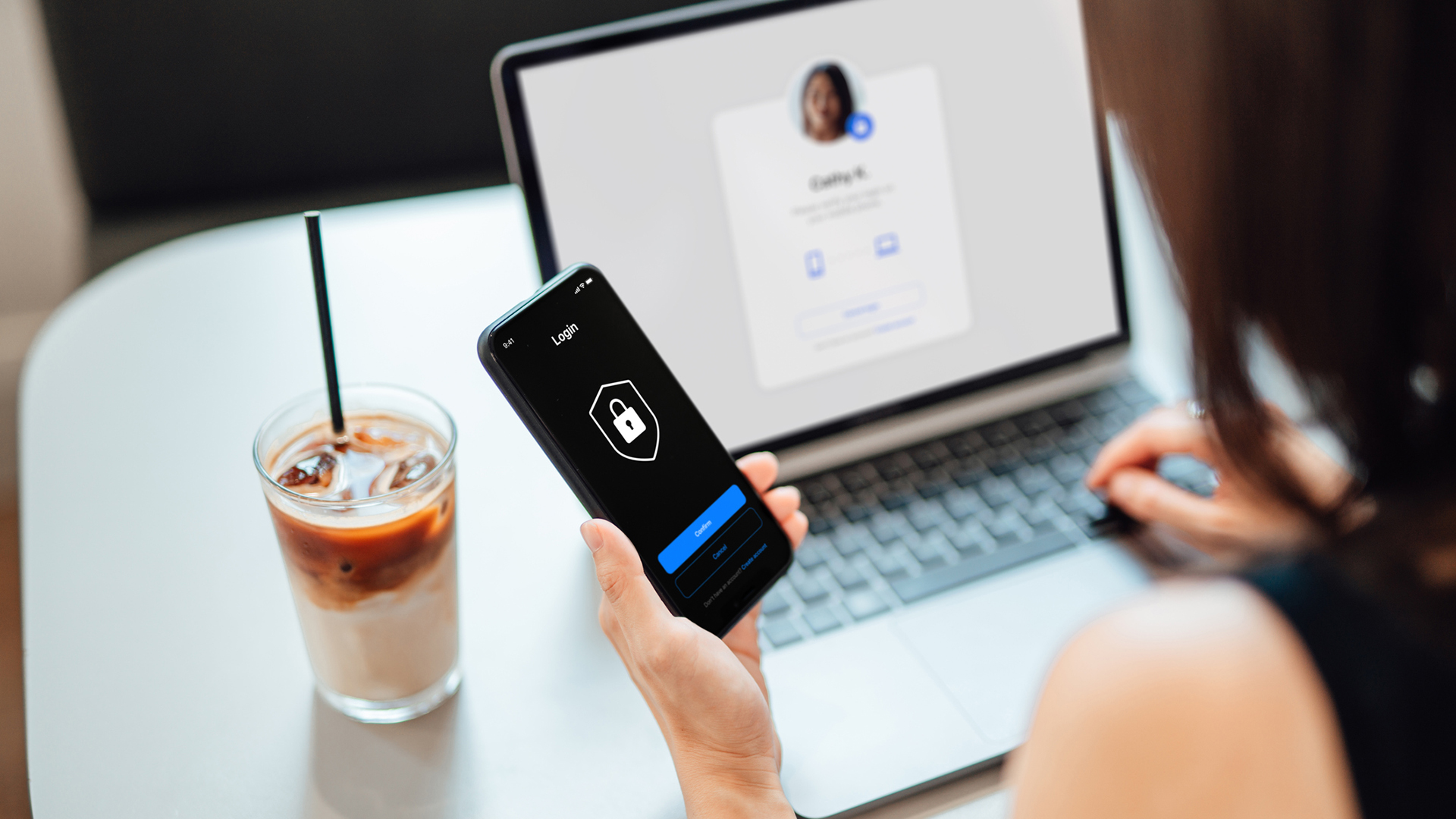
Every employee should create strong passwords using messages, special characters, and numbers and combine them with multi-gene hallmark to prevent unauthorized admission to their devices. Companies may opt to employ passphrases instead to provide additional system security.
Passphrases are longer and more complex, using a mix of unrelated, capitalized, and lowercase words, numbers, and special characters to make it more than challenging for a hacker to breach an account. About importantly, don't utilize the same passwords or passphrases throughout the company, and remember to prepare a password to secure your Wi-Fi network.
Consider subscribing to a reliable and secure countersign managing service for easier admission to your accounts. These password managers can too generate complex passwords for you.
8. Perform a regular audit of your cyber protection procedures

Waiting for an attack to happen to confirm whether your security protocols are working is a recipe for disaster. Review your cybersecurity policies and regularly cheque the software, systems, servers, and cloud solutions to ensure your business organization is fully secured. Access backed-up files and download them to run across how the recovery process volition work for your business.
Identify whatsoever vulnerabilities and resolve them and ostend whether the backed-upwards files have been corrupted in any way. Perform other maintenance acts like removing unused software to reduce the risk of cybercriminals exploiting it to steal or destroy your sensitive data. Talk to law enforcement to learn more almost ransomware—malicious software used to hijack data and extort coin from the victims—to know how to prevent information technology from happening.
Update all passwords and passphrases if devices are lost or compromised. Check Internet of Things (IoT) connected smart devices, such equally temperature control devices, to know what data they are collecting and whether they can be exploited, posing a risk to the business organisation.
9. Scan and monitor networks to prevent breaches

Implementing cyber protection policies can prevent data breaches from occurring. Offset, uninstall older software and remove old devices, which can be exploited if they can't be upgraded to the latest operating software. Ensure they don't have sensitive information stored before getting rid of them.
Purge the arrangement of onetime admission codes and passwords to forestall former employees from unauthorized access to steal or destroy your data. Scan portable disks earlier inserting them into your computers in case they have viruses that tin give criminals admission to your systems.
Limit administrative calculator privileges to higher-ranking employees and IT experts to end criminals from compromising employees and gaining access to more information than they predictable. Ensure employees can't install software or access unsecured websites without authority to avoid harmful tertiary-political party app installations and viruses infiltrating your systems.
x. Establish mutual cybersecurity policies with business partners

It is vital to take cybersecurity policies that match or complement those of your business partners. Coordinating online safety measures can shut potential loopholes, ensuring the cyber vulnerability doesn't come from inside your circle. Bank check each other's privacy policy guidelines to ensure everyone is complying with manufacture and regulatory standards on handling data.
Browse emails and documents from business organisation partners to block malware, and encrypt all information when receiving or transferring files. Consult your concern partners on their cybersecurity success stories and prefer similar measures where applicable to guarantee that no cyber threats volition get through your defenses.
Summary
Preventing a cyberattack is crucial for your business concern's survival. Information technology takes a lot of time, money, and effort to recover from a cyberattack, and you'll need to work with the relevant authorities to resolve the issue and ready up new systems to thwart hereafter threats.
The business organization volition endure reputational damage if it loses customer data or fails to alert them early about a alienation. Companies that rely on your business for their operations will also be hurt in the procedure. Utilize the steps listed above to shield your business organisation, secure your data, and protect your customers.
Read this related article to acquire more than about endpoint security.
Is Sharing Security Data The Best Way To Deter Cyber Criminals?,
Source: https://www.itproportal.com/features/10-effective-steps-for-preventing-cyberattacks-on-your-business/
Posted by: cokleyunfortuabood.blogspot.com



0 Response to "Is Sharing Security Data The Best Way To Deter Cyber Criminals?"
Post a Comment